OAuth 1.0
OAuth 2.0
OAuth 2.0 released in October 2012 to overcome the problem as specified above in OAuth 1.0. The OAuth 2.0 authorization framework allows a third-party application to gain limited access to an HTTP service, either on behalf of a resource owner by orchestration of an approval agreement between the resource owner and the HTTP service, or by requiring the third-party application to obtain access on its own behalf
Difference between OAuth 1.0 and OAuth 2.0
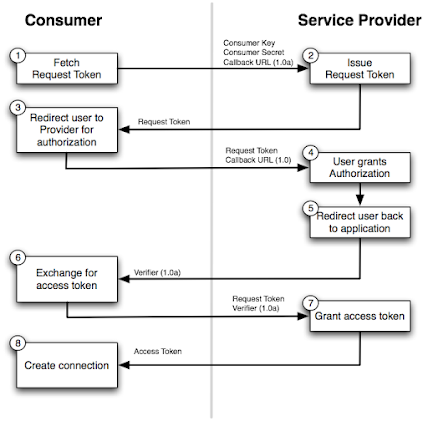
OAuth 1.0 Flow
- Client application registers with provider, such as Twitter.
- Twitter provides client with a “consumer secret” unique to that application.
- Client app signs all OAuth requests to Twitter with its unique “consumer secret.”
- If any of the OAuth request is malformed, missing data, or signed improperly, the request will be rejected.
OAuth 2.0 Flow
- Client application registers with provider, such as Twitter.
- Twitter provides client with a “client secret” unique to that application.
- Client application includes “client secret” with every request commonly as http header.
- If any of the OAuth request is malformed, missing data, or contains the wrong secret, the request will be rejected.
Detailed Explanation
Security of the OAuth 1.0 protocol (RFC 5849) relies on the assumption that a secret key embedded in a client application can be kept confidential. However, the assumption is naive.
In that sense, OAuth 1.0 is a specification only for confidential clients.
"OAuth 2.0 and the Road to Hell" says that OAuth 2.0 is less secure, but there is no practical difference in security level between OAuth 1.0 clients and OAuth 2.0 confidential clients. OAuth 1.0 requires to compute signature, but it does not enhance security if it is already assured that a secret key on the client side can be kept confidential. Computing signature is just a cumbersome calculation without any practical security enhancement. I mean, compared to the simplicity that an OAuth 2.0 client connects to a server over TLS and just presents
client_id and client_secret, it cannot be said that the cumbersome calculation is better in terms of security.In addition, RFC 5849 (OAuth 1.0) does not mention anything about open redirectors while RFC 6749 (OAuth 2.0) does. That is,
oauth_callback parameter of OAuth 1.0 can become a security hole.Therefore, I don't think OAuth 1.0 is more secure than OAuth 2.0.
OAuth 1.0 security relies on signature computation. A signature is computed using a secret key where a secret key is a shared key for HMAC-SHA1 (RFC 5849, 3.4.2) or a private key for RSA-SHA1 (RFC 5849, 3.4.3). Anyone who knows the secret key can compute the signature. So, if the secret key is compromised, complexity of signature computation is meaningless however complex it is.
This means OAuth 1.0 security relies not on the complexity and the logic of signature computation but merely on the confidentiality of a secret key. In other words, what is needed for OAuth 1.0 security is only the condition that a secret key can be kept confidential. This may sound extreme, but signature computation adds no security enhancement if the condition is already satisfied.
Likewise, OAuth 2.0 confidential clients rely on the same condition. If the condition is already satisfied, is there any problem in creating a secure connection using TLS and sending
client_id and client_secret to an authorization server through the secured connection? Is there any big difference in security level between OAuth 1.0 and OAuth 2.0 confidential clients if both rely on the same condition?I cannot find any good reason for OAuth 1.0 to blame OAuth 2.0.
OAuth 2 delegates security to the HTTPS protocol. OAuth 1 did not require this and consequentially had alternative methods to deal with various attacks. These methods required the application to engage in certain security protocols which are complicated and can be difficult to implement. Therefore, it is simpler to just rely on the HTTPS for security so that application developers dont need to worry about it.
As to your other questions, the answer depends. Some services dont want to require the use of HTTPS, were developed before OAuth 2, or have some other requirement which may prevent them from using OAuth 2. Furthermore, there has been a lot of debate about the OAuth 2 protocol itself. As you can see, Facebook, Google, and a few others each have slightly varying versions of the protocols implemented. So some people stick with OAuth 1 because it is more uniform across the different platforms. Recently, the OAuth 2 protocol has been finalized but we have yet to see how its adoption will take.
Refer link :


https://www.techgeeknext.com/spring-boot-security/oauth-2-0-vs-oauth-1-0
ReplyDelete